Revisiting the Linux Score Distribution
A while back, we showed what the score distributions were for base installs of three major platforms. Here, we're going to compare that base install view of Linux with the score distribution for a custom, hardened instance of Linux. To refresh memories, here was the original Linux distribution:
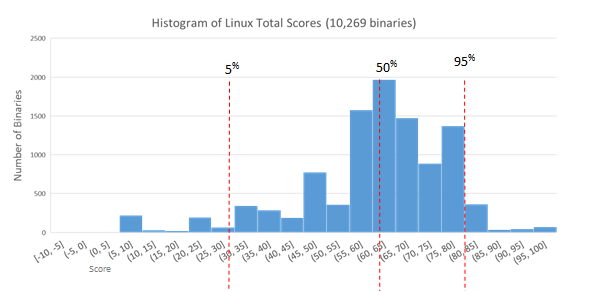
And here is the score distribution for our customized, hardened version of Linux:
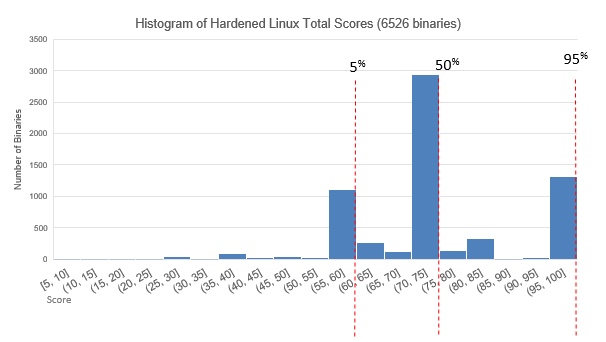
There are no longer any negative scores, and the overall score distribution has greatly improved. These numbers can be compared directly, because they're both from environments with the same set of possible safety features, and all features are weighted the same.
As we saw with Windows, you can tell from the histogram of the hardened Linux instance that the build practices were more uniform because the binaries are much more clustered than before. This customization largely consisted of re-compiling all of the binaries with all possible application armoring features enabled to reasonable degrees. Bad functions or programming errors in the source code were not addressed, because the source code was not changed, but all available safety features are now being applied across the board. It should be noted that this hardened Linux build still lacks certain Kernel safety features (e.g. not all of the PAX/GRSec Kernel mods were enabled) as some would have interfered with necessary operations. This is just a reasonably hardened, but entirely usable Linux instance.
The ability to easily customize and harden the default distribution of Open Source Operating Systems should be a big draw for organizations that want to improve their security stance. With closed source software, the consumer has to hope that the vendor in question knows what they're doing when it comes to build environment and settings (Microsoft Windows 10 did well in this regard when compared with default OS X and Linux builds). The results usually end up being mixed and somewhat mediocre. The off the shelf quality of open source build practices isn't much better, as shown by the distribution for Ubuntu above, but then at least the consumer can redo it on their own and know it was done right. This sort of customization may be out of scope for many smaller businesses, unless they are security conscious and technically capable. It is, however, a completely reasonable behavior for larger organizations. So, why is it that most large corporations are not engaging in this security practice? After all, doing this measurably increases the difficulty and cost for an adversary to exploit the more uniform (hardened) environment.
We believe that there are two major contributing factors that prevent organizations from engaging in the practice of customizing and hardening their builds of open source distributions. First, of course, they might not know or think to do so. After all, there is a lot of ignorance and learned helplessness out there, and consumers of all types and sizes have been conditioned to just accept the software they are given, and not think of tinkering or customizing it for their needs.
Second, though, most corporations do not have any significant incentive to engage in this practice. It might improve their security, but it is viewed as a cost in the short term to put in the effort. If the weaker security stance results in a breach, well, that is why they have insurance... right?
This wouldn't fly for most other types of risk management. High value insurance policies can get pretty specific about what actions and levels of effort need to be taken by the insured to protect their property and prevent loss or damage. The insurance company knows, for example, the TL-ratings for the safes used in high-value environments. If the safe's rating says that it should last for about 30 minutes (TL-30) against common attacks, then the policy may require that a security guard pass by at least every 25 minutes.
This sort of system incentivizes companies to protect themselves as much as reasonably possible. It is one of the reasons why large organizations also have large physical security infrastructures that are customized for their business and environment. A large multinational corporation doesn't just put a "Secured by ___ Home Security" sticker in their window and call it a day. But, when it comes to cyber security practices, many corporations are frequently doing the equivalent, because cyber insurance policies are not requiring that they do more.
With these measurements and analytics, and the more detailed static, dynamic, and predictive ones to come, we hope to help address this issue.
